Saturday, 26 June 2010
Maliciously scripted
If you’re gonna do this:
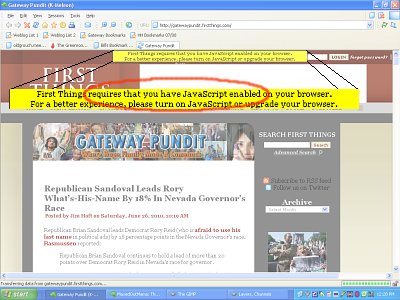
...then you had better watch out for this:
Of course the networks would scream, but they’ve repeatedly.been.found to be untrustworthy.
And since we seem doomed to a bright new javascript-required-for- even-minimal-functionality web[1], wouldn’t it be nice if some browser creator would come up with javascript controls that give us greater granularity than No Scripts At All/All Scripts? Possibly one that blocked any scripts not originating within the parent domain, or maybe even one that could be configured to block (or at least warn) when some of the language’s more problematic functions (“eval,†anyone?) are called?
Elsewhere:
(Via)
------
Comments are disabled.
Post is locked.
If you’re gonna do this:

...then you had better watch out for this:
First Things website had a Malware attack today. We are working on the problem now. The warning messages should go away by tomorrow afternoon. We have removed the ad script that was causing the problem so there is no chance that you will get an infected browser. It looks like if you run Internet Explorer you won’t see the warning messages but, with Chrome, Safari or Firefox you will still see the messages.Not a new problem, and in most cases fixable by not permitting scripting code that originates from (or receives variables from) third-party sources, i.e., ad networks.
By the way, the attack came from China.
Of course the networks would scream, but they’ve repeatedly.been.found to be untrustworthy.
And since we seem doomed to a bright new javascript-required-for- even-minimal-functionality web[1], wouldn’t it be nice if some browser creator would come up with javascript controls that give us greater granularity than No Scripts At All/All Scripts? Possibly one that blocked any scripts not originating within the parent domain, or maybe even one that could be configured to block (or at least warn) when some of the language’s more problematic functions (“eval,†anyone?) are called?
Elsewhere:
(Via)
------
[1] I note the FirstThings site currently loads 10 internal scripts plus three adserver scripts.
Posted by: Old Grouch in
In Passing
at
17:48:50 GMT
| No Comments
| Add Comment
Post contains 234 words, total size 4 kb.
70kb generated in CPU 0.2987, elapsed 1.1606 seconds.
51 queries taking 1.0669 seconds, 207 records returned.
Powered by Minx 1.1.6c-pink.
51 queries taking 1.0669 seconds, 207 records returned.
Powered by Minx 1.1.6c-pink.














