Wednesday, 08 April 2009
Pro-“Cybergrab†bill propaganda begins
On Sunday I wrote about the S.773/S.778 “Cybergrab†bills being perpetrated in the name of “security†by Senators John Rockefeller (D-WV) and Olympia Snowe (R-ME). Today the Wall Street Journal chimes in with a mostly-content-free front-page article which attempts to stoke the paranoia up another notch by using generalities, innuendo, irrelevant examples, confusion, and off-the-record sources. Lots of propaganda, little substance.
Deconstruction proceeds below the break...


The Journal:
Two paragraphs down, we read:
Okay, time out. It is perfectly plausible to assume that foreign espionage agents are out there, sniffing around our infrastructure.[1] I would go further to say that an absence of reports of such activity would be grounds for indicting the FBI and the Department of Homeland Security for incompetence. It is also likely that some foreign agent, should he gain access to the systems involved, would leave some sort of “logic bomb†behind, if he could.[2] So it is only prudent to take precautions.
IMO it is also likely that the power generation and distribution folks could use a bit of shaking up. Power system control, in part because it has traditionally been isolated from public access, lacks a tradition of being “secure by design†when it comes to sabotage, unauthorized access, or the introduction of false data by intruding parties,[3] so it’s at least worth raising the issue. The financial guys... I'm not so concerned. Dealing with large amounts of money tends to concentrate the mind, and all that. Plus, the financial people began taking measures against the possibility of criminals injecting false data into their networks early on, which puts them ahead of the distribution people.
But do I have to mention yet again that “a network†=/= “the Internet�
Anyway, before we get off the front page, the Journal includes this otherwise unexplained graphic.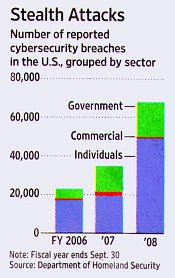
At first glance, it looks scary. The number of “reported cybersecurity breachesâ€[4] approximately triple– going from just over 20,000 to just under 70,000– when comparing fiscal year 2008 with fiscal year 2006.
But the sectors with big problems are Individuals (where the p3na9e more than doubled) and Government (where breaches more than tripled). Meanwhile, in the “Commercial sector,†the one the Journal’s article is all flustered about, breaches increased in 2007, then fell back to approximately 2006 levels in 2008.[5]
And note that this shows “reported cybersecurity breaches.†Are these “breaches†the same thing as the earlier “intrusions,†or do those numbers include stolen laptops, missing backup tapes, unencrypted discs losts in the mail, schools posting student social security numbers on their websites, charge card slips dug out of dumpsters, and the like?
(And that assumes the DHS’s numbers are even accurate. But here they’re being offered in support of intrusive legislation. Might this be another BATFE-style “90% of the guns confiscated from Mexican drug gangs come from the U.S.†statistic? Perhaps a grain of salt is in order.)
Okay, back to the Journal...
Okay, granting that there’s - “probably,†for the sake of argument - a concern here: What to do, what to do...?
Taa-da: Government To The Rescue!
Anyway, after some blah-blah about goings on overseas, including
Despite the fact that the Federal Energy Regulatory Commission mandated improved computer security for transmission/generation companies a year ago (in January, 2008).[7] That the grid operators are already upgrading security to meet the new standards.[8] And that the North American Electric Reliability Corporation, the power industry’s “independent standards-setting organization overseen by the Federal Energy Regulatory Commission,†implemented a standard that requires power companies identify their “critical cyber assets,†also- a year ago.[9]
So, is there a need or not? Certainly the casual reader might be convinced that there is. But, specifically, is this legislation the answer? No. With its tremendous expension of executive power, vague limits, mandated changes, and certification requirements, it’s yet another case of the Democrats “never failing to take advantage of a good crisis.†Which, unfortunately, you won’t find out from this Journal story.
Elsewhere (added 090409 19:17):
Previously:
------
[1] I just hope that the CIA is returning the favor.
[2] We may already have done this ourselves. There’s a persistent rumor that booby-trapped electronic controllers introduced by the CIA caused a pipeline explosion in the Soviet Union a number of years ago.
[3] Power distribution and plant control systems are very secure when you’re talking about protecting system integrity or failing in a safe manner.
[4] Given the low Individual sector numbers (approx. 50,000 in 2008), I would assume that the DHS restricts “attack†to events that are more severe than the common or garden virus infection or botnet capture.
[5] It’s difficult to say whether 2008 was better or worse than 2006. What is obvious is that the Commercial sector is barely visible in either the 2006 or 2008 bars.
[6] A decent summary of what the saboteur did is about halfway down this 2002 Washington Post article (scroll to 'Could have done anything'). Geeks may want to check out the National Institute of Standards and Technology-hosted case study (PDF).
[7] Reported in paragraph 19 of 24.
[8] Reported in paragraph 18 of 24.
[9] Reported in paragraph 24 of 24. Are you noticing a pattern here?
Comments are disabled.
Post is locked.
On Sunday I wrote about the S.773/S.778 “Cybergrab†bills being perpetrated in the name of “security†by Senators John Rockefeller (D-WV) and Olympia Snowe (R-ME). Today the Wall Street Journal chimes in with a mostly-content-free front-page article which attempts to stoke the paranoia up another notch by using generalities, innuendo, irrelevant examples, confusion, and off-the-record sources. Lots of propaganda, little substance.
Deconstruction proceeds below the break...


The Journal:
Cyberspies have penetrated the U.S. electrical grid and left behind software programs that could be used to disrupt the system, according to current and former national-security officials.So it begins. And, as we learn from “former national-security officials,†the spies, “from China, Russia, and other countries,†are “believed†to be “attempting to map our infrastructure, such as the electrical grid.â€
Two paragraphs down, we read:
“There are intrusions, and they are growing...There were a lot last year.â€And (according to the same unnamed officials) the companies involved were clueless.
Many of the intrusions were detected not by the companies in charge of the infrastructure but by U.S. intelligence agencies, officials said. Intelligence officials worry about cyber attackers taking control of electrical facilities, a nuclear power plant or financial networks via the Internet.Note the way that last sentence builds the anxiety: Suddenly it’s not just the electricity grid, it’s (cue scary music) nuclear power plants and (more scary music) “financial networks†and (Aieeee!) it’s all “via the Internetâ€! What’s more...
Authorities investigating the intrusions have found software tools left behind that could be used to destroy infrastructure components, the senior intelligence official said. He added, “If we go to war with them, they will try to turn them on.â€
Okay, time out. It is perfectly plausible to assume that foreign espionage agents are out there, sniffing around our infrastructure.[1] I would go further to say that an absence of reports of such activity would be grounds for indicting the FBI and the Department of Homeland Security for incompetence. It is also likely that some foreign agent, should he gain access to the systems involved, would leave some sort of “logic bomb†behind, if he could.[2] So it is only prudent to take precautions.
IMO it is also likely that the power generation and distribution folks could use a bit of shaking up. Power system control, in part because it has traditionally been isolated from public access, lacks a tradition of being “secure by design†when it comes to sabotage, unauthorized access, or the introduction of false data by intruding parties,[3] so it’s at least worth raising the issue. The financial guys... I'm not so concerned. Dealing with large amounts of money tends to concentrate the mind, and all that. Plus, the financial people began taking measures against the possibility of criminals injecting false data into their networks early on, which puts them ahead of the distribution people.
But do I have to mention yet again that “a network†=/= “the Internet�
Anyway, before we get off the front page, the Journal includes this otherwise unexplained graphic.

At first glance, it looks scary. The number of “reported cybersecurity breachesâ€[4] approximately triple– going from just over 20,000 to just under 70,000– when comparing fiscal year 2008 with fiscal year 2006.
But the sectors with big problems are Individuals (where the p3na9e more than doubled) and Government (where breaches more than tripled). Meanwhile, in the “Commercial sector,†the one the Journal’s article is all flustered about, breaches increased in 2007, then fell back to approximately 2006 levels in 2008.[5]
And note that this shows “reported cybersecurity breaches.†Are these “breaches†the same thing as the earlier “intrusions,†or do those numbers include stolen laptops, missing backup tapes, unencrypted discs losts in the mail, schools posting student social security numbers on their websites, charge card slips dug out of dumpsters, and the like?
(And that assumes the DHS’s numbers are even accurate. But here they’re being offered in support of intrusive legislation. Might this be another BATFE-style “90% of the guns confiscated from Mexican drug gangs come from the U.S.†statistic? Perhaps a grain of salt is in order.)
Okay, back to the Journal...
“Over the past several years, we have seen cyberattacks against critical infrastructures abroad, and many of our own infrastructures are as vulnerable as their foreign counterpartsâ€...Contention not proven, but, just for the sake of argument, let’s proceed...
Director of National Intelligence Dennis Blair recently told lawmakers. “A number of nations, including Russia and China, can disrupt elements of the U.S. information infrastructure.â€Well finally, somebody on the record! But note the nuance: Blair says “information infrastructure.†Waitaminnit. Up above it was all about the electrical grid, and water and sewage systems. “Information infrastructure,†electric grid, water system, sewage system... one of these is not the same as the other! (Sounds like we’re back to the Internet, again.) And regardless, if, as Blair says, all those foreigners “can disrupt†our systems, then is it safe to assume that we know how they can? And that we ARE doing something about it?
Okay, granting that there’s - “probably,†for the sake of argument - a concern here: What to do, what to do...?
Taa-da: Government To The Rescue!
...protecting the electrical grid and other infrastructure is a key part of the Obama administration’s cybersecurity review, which is to be completed next week. Under the Bush administration, Congress approved $17 billion in secret funds to protect government networks, according to people familiar with the budget. The Obama administration is weighing whether to expand the program to address vulnerabilities in private computer networks,...I’ll just bet they are...
which would cost billions of dollars more. A senior Pentagon official said Tuesday the Pentagon has spent $100 million in the past six months repairing cyber damage.(And, as an aside, that last sentence has what, exactly, to do with the one preceding it?)
Anyway, after some blah-blah about goings on overseas, including
...In 2000, a disgruntled employee rigged a computerized control system at a water-treatment plant in Australia, releasing more than 200,000 gallons of sewage into parks, rivers and the grounds of a Hyatt hotel.(Largely irrelevant, because it was an inside job, although Maroochy Shire- the owner of the plant in question- and its contractors could have done better at securing their system from unauthorized access.[6]), we get a survey of the U.S. electrical system, more unsourced quotes about “intrusions,†and (expected) denials from the Russians and Chinese. Then, at last, we come to the payoff:
Last week, Senate Democrats introduced a proposal...There It Is, Folks!
...that would require all critical infrastructure companies to meet new cybersecurity standards and grant the president emergency powers over control of the grid systems...because people and companies are so bad at looking out for their own stuff...
and other infrastructure.Like, well, you name it...
Despite the fact that the Federal Energy Regulatory Commission mandated improved computer security for transmission/generation companies a year ago (in January, 2008).[7] That the grid operators are already upgrading security to meet the new standards.[8] And that the North American Electric Reliability Corporation, the power industry’s “independent standards-setting organization overseen by the Federal Energy Regulatory Commission,†implemented a standard that requires power companies identify their “critical cyber assets,†also- a year ago.[9]
So, is there a need or not? Certainly the casual reader might be convinced that there is. But, specifically, is this legislation the answer? No. With its tremendous expension of executive power, vague limits, mandated changes, and certification requirements, it’s yet another case of the Democrats “never failing to take advantage of a good crisis.†Which, unfortunately, you won’t find out from this Journal story.
Elsewhere (added 090409 19:17):
Readers at The Register gets their licks in.
Previously:
------
[1] I just hope that the CIA is returning the favor.
[2] We may already have done this ourselves. There’s a persistent rumor that booby-trapped electronic controllers introduced by the CIA caused a pipeline explosion in the Soviet Union a number of years ago.
[3] Power distribution and plant control systems are very secure when you’re talking about protecting system integrity or failing in a safe manner.
[4] Given the low Individual sector numbers (approx. 50,000 in 2008), I would assume that the DHS restricts “attack†to events that are more severe than the common or garden virus infection or botnet capture.
[5] It’s difficult to say whether 2008 was better or worse than 2006. What is obvious is that the Commercial sector is barely visible in either the 2006 or 2008 bars.
[6] A decent summary of what the saboteur did is about halfway down this 2002 Washington Post article (scroll to 'Could have done anything'). Geeks may want to check out the National Institute of Standards and Technology-hosted case study (PDF).
[7] Reported in paragraph 19 of 24.
[8] Reported in paragraph 18 of 24.
[9] Reported in paragraph 24 of 24. Are you noticing a pattern here?
Posted by: Old Grouch in
Rants
at
14:29:20 GMT
| No Comments
| Add Comment
Post contains 1469 words, total size 17 kb.
83kb generated in CPU 0.2045, elapsed 0.5394 seconds.
51 queries taking 0.5278 seconds, 207 records returned.
Powered by Minx 1.1.6c-pink.
51 queries taking 0.5278 seconds, 207 records returned.
Powered by Minx 1.1.6c-pink.














